There is no doubt that flash memory is one of the easiest and best ways to store and transfer files that can be used. Despite its small size and lightweight, it can accommodate a lot of files and data that may reach a terabyte in size, in addition to its ease of use, relatively low cost, and ability to transfer data at high speed. It can even be used to run Windows directly from it.
Encrypt flash memory on the computer
However, in a way, flash memory units have become more vulnerable to loss or theft, which poses a serious threat to the security of the data and files stored in them, which may fall into the hands of the wrong people to misuse them. Therefore, it is always recommended to encrypt the flash memory to protect the data and files it contains and prevent others. access and misuse. Many programs and applications can perform this task efficiently, and below we review the best ways to encrypt flash memory on the computer.
First: Why do we need to encrypt flash memory?
Encrypting our files and data is an effective way to prevent others from violating our privacy and accessing them without our consent, especially if those files include highly sensitive personal data such as financial transactions and credit card data. Encryption mainly aims to make these data and files unreadable unless the user enters a pre-set password to verify that he is the real owner of the device.
Flash memory encryption can protect our data and information from hackers if the flash memory is left or forgotten somewhere, as well as if it is lost or stolen. An encrypted flash memory can become a worthless tool for any user other than its original owner. Although it can be formatted, others will not be able to know which files it contains.
Second: The mechanism used in encryption programs
The most common encryption type used in volume encryption programs is AES-256 encryption, which is a strong encryption mechanism that enables you to convert your files and data into an unreadable version and assign a password to it so that it can only be decrypted and operated by people who have the password. If AES-256 encryption is used, cyberattackers and hackers may need up to a billion years of attempts to decrypt data.
Other encryption mechanisms are older, some of which have become obsolete after modern computers became able to hack them quickly, such as the SHA-1, MD2, MD4, MD5, and DES/3DES encryption mechanisms, and the use of encryption programs that rely on these mechanisms has become a huge security risk. Data is stored in storage units of various types due to the ease of decryption.
Third: Ways to encrypt flash memory
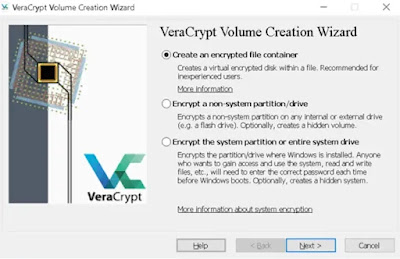
1- VeraCrypt program
VeraCrypt is one of the strongest and best encryption programs available and is a completely free encryption tool. VeraCrypt uses open-source algorithms that are constantly being developed and verified for security and provides more than one encryption method that the user can choose from, such as Serpent, Twofish, Camellia, and AES. The program's work is not limited to encrypting flash memory and USB devices, it can also encrypt SSD, and it can encrypt multiple flash drives very quickly and in a short time.
A very easy user interface characterizes the program and is available for use in several languages. It allows the user to create hidden folders within a folder that is opened with a separate password. Even if a hacker succeeds in opening the flash memory or forces you to enter its password, he will only find an empty folder in front of him It contains misleading and unimportant files inside, while the most important files and data remain safe and cannot be accessed by hackers.
The program also provides another similar feature, which is the secret operating system feature, which enables the user to hide his files in hidden folders that can only be viewed on a specific version of the operating system. Versions of VeraCrypt are available that are compatible with Windows, Mac, Linux, Unix, and Raspberry operating systems, but the program must be installed on all computers that we may want to use to run the encrypted flash memory to be able to decrypt it and access its content.
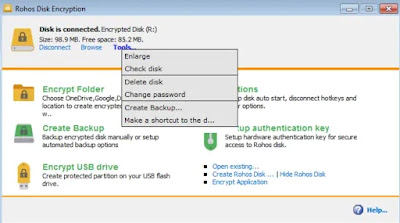
2- Rohos Disk Encryption program
The Rohos program is characterized by lightness and ease of use. It is a completely free program that is compatible with Windows only and uses the AES 256 encryption algorithm. There are two main products from Rohos, one of which is Rohos Disk Encryption, which allows users to encrypt flash memory units and even cloud storage tools and the other version is a Rohos Logon Key that can turn your flash memory or smartphone into a security key to decrypt the flash memory encrypted using Rohos Disk Encryption.
The RuHoS interface provides a list of customizable settings that help you create backup copies of your files, allow you to encrypt flash memory and even encrypt applications, and allow you to camouflage encrypted memories and devices so that they appear as files in deceptive formats such as Mp4 or Mp3. All you have to do is install the program on your computer, then connect the hard disk or flash memory that needs to be encrypted so that the Ruhos program can detect the connected device and start suggesting the best available settings.
3- AxCrypt program
AxCrypt has an easy-to-use interface for inexperienced users and offers flash memory encryption features using AES-256 encryption. XScript provides auto-encryption and allows caching of passwords. There is a commercial version of the program in addition to the version intended for individuals. This version focuses on supporting corporate activities and also provides a master password for entrepreneurs and workers.
Versions of the program are available that are compatible with Windows and Mac operating systems. There is a trial version of the program available to install and use on both systems for free with limited features for a specific period, while the paid version of the application requires paying a monthly subscription fee of up to 4 US dollars, but it has unlimited features.
4- Gilisoft program
For non-professional users, Gilisoft USB Encryption is one of the best encryption tools available that is compatible with Windows operating systems, thanks to its very simple user interface that provides encryption features that are easy to handle even for those with little experience with this type of software, and it also provides a recovery feature. data.
Gelisoft is a program specialized in encrypting flash memory units and other external storage devices and provides different layers of protection to lock the content of these devices using AES-256 encryption algorithms. So far, the program is only compatible with Windows operating systems, and there is a trial version available that can be installed and used for free for a limited time, but the full version of the program is paid and its purchase cost may reach 50 US dollars.
5- BitLocker To Go program
BitLocker To Go comes as a free encryption tool built into the Pro and Enterprise editions of Windows. This tool can provide quick encryption of storage units, including internal and external hard drives, flash memory, and SD cards. It is an easy-to-use encryption tool that only requires you to connect the flash memory to the device, then right-click on it from the File Explorer tool and choose “Turn on BitLocker.” You then set a password for it so that the tool encrypts the device using the AES-256 encryption pattern within a few seconds.
The tool is particularly suitable for Windows users who do not wish to install any additional software or use paid applications, but the program does not provide the possibility of remote operation, which means that it is a local encryption mechanism that can only play encrypted flash memory units locally on the computer to which it is already connected. Which is not appropriate for use in large companies and institutions that manage remote workers’ devices centrally.
There is a similar tool that performs the same tasks for Mac users, which is the FileVault tool, which is integrated into Mac operating systems and does not require additional downloads, installations, or payments.
Most encryption software and tools also provide a Recovery Key as a way to regain access to encrypted devices if their passwords are lost or forgotten. The recovery code may be a password or a long string of random words that the user can enter in order to recover the device's password. If the device's recovery code is lost or lost, the user may permanently lose access to the data stored on this device.
Encrypt flash memory on the computer
If some files stored in encrypted flash memory are lost or fail to play, this problem can be easily remedied by installing the Wondershare Recoverit program on the computer, inserting the flash memory into the computer, selecting it in the program, and then the program scans the device for deleted items. So you can get it back.






Post a Comment